This is a step-by-step instruction of how to install Let's Encrypt SSL with NginX on your Ubuntu 16.04 or Ubuntu 18.04 (both are popular LTS releases). I will try to describe several useful settings that will make configuration easy and smart. I will use different commands that will be executed due to the Ubuntu version differences. Those blocks will be highlighted so pay attention to that, but almost everything should be the same.
You need Ubuntu 16.04 or Ubuntu 18.04 server with SSH access, a registered domain name pointed to your server's IP, and a small portion of the knowledge of how to use a Linux console and execute commands on the Ubuntu server. The whole installation will take around 30 minutes.
Before installing new soft you should always consider updating the package list in order to have your software up to date.
sudo apt-get update
Add software repository Ubuntu 16.04
sudo apt-get install software-properties-common python-software-properties
sudo add-apt-repository ppa:certbot/certbot
sudo apt-get update
Add software repository Ubuntu 18.04
sudo apt-get install software-properties-common
sudo add-apt-repository ppa:certbot/certbot
sudo apt-get update
Installation
For now, everything is ready to install LetsEncrypt on your server:sudo apt-get install letsencrypt
This command will install letsencrypt dummy package that includes certbot and other utilities for SSL installation.
In my configuration examples, I will use the following domain name 'ssl.itsyndicate.org'. Do not forget to change it for your needs when you do a copy-paste. Now it's time for a small life-hack that will show you how to optimize the process of adding new certificates to your server. We will use Nginx default config to catch all requests with non-secure connections that are going to our server aka non-ssl which will target 80 port.
server {
listen 80 default_server;
server_name _;
location ~ /\.well-known/acme-challenge/ {
allow all;
root /var/www/letsencrypt;
try_files $uri =404;
break;
}
}
As you can see we are using /\.well-known/acme-challenge/ directory to catch all requests for location and /var/www/letsencrypt directory to host acme-challenges. So let's create directory after you edited the default NginX vhost config:
sudo mkdir -p /var/www/letsencrypt
Before applying changes to your NginX settings always check configuration file:
sudo nginx -t
You should get a notification that syntax is ok:
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
To apply changes to our new Nginx vhost configuration that is designed to catch all of your Let's Encrypt certificates challenges do the following:
sudo service nginx reload
Step 3 - Request new Let's Encrypt SSL
Now it is time to request our first Let's Encrypt SSL certificate for our domain:
sudo letsencrypt certonly -a webroot --webroot-path=/var/www/letsencrypt -m mail@example.com --agree-tos -d ssl.itsyndicate.org
Let me describe some important options in our command:
--webroot-path=/var/www/letsencrypt - here we configure a directory where all requests will be stored. We configured NginX to serve this directory.
-m mail@example.com - with this option you are setting up your e-mail address
--agree-tos - this option is needed not to prepare TOS and to accept them. This is some kind of fully automated way to install Let's Encrypt SSL
-d ssl.itsyndicate.org - this option is used to issue SSL for the desired domain
After command execution you should see Congratulations message:
IMPORTANT NOTES:
- If you lose your account credentials, you can recover through
e-mails sent to mail@example.com.
- Congratulations! Your certificate and chain have been saved at
/etc/letsencrypt/live/ssl.itsyndicate.org/fullchain.pem. Your cert
will expire on 2018-08-01. To obtain a new version of the
certificate in the future, simply run Let's Encrypt again.
- Your account credentials have been saved in your Let's Encrypt
configuration directory at /etc/letsencrypt. You should make a
secure backup of this folder now. This configuration directory will
also contain certificates and private keys obtained by Let's
Encrypt so making regular backups of this folder is ideal.
- If you like Let's Encrypt, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
Step 4 - Configure NginX vhost
Now we have new SSL installed to '/etc/letsencrypt/live/ssl.itsyndicate.org/'. It's time to configure our Nginx vhost to serve https requests for the desired domain. Here is my example:
server {
server_name itsyndicate.org;
listen 443 ssl;
ssl on;
ssl_certificate /etc/letsencrypt/live/ssl.itsyndicate.org/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/ssl.itsyndicate.org/privkey.pem;
root /var/www/html/;
index index.php index.html index.htm;
location ~ /.well-known {
root /var/www/letsencrypt;
allow all;
}
}
Let's test and reload our new Nginx configuration:sudo nginx -t
sudo service Nginx reload
Step 5 - Configure Let's Encrypt SSL auto-renewal
Let's Encrypt issues certificates for 90 days. You have an opportunity to reinstall it manually when you got the email that your SSL expires soon, but I think there is a smart way to automate that. We will use daily cron on our Ubuntu server to renew our SSL certificate. Due to the different versions of the letsencrypt package in Ubuntu 16.04 and Ubuntu 18.04, I will use different renewal commands.
Ubuntu 16.04 Let's Encrypt renewal
I use '/etc/cron.daily/letsencrypt' file to setup cron with the following content:
#!/bin/bash
/usr/bin/letsencrypt renew && /etc/init.d/nginx reload
Ubuntu 18.04 Let's Encrypt renewal
I use the same file '/etc/cron.daily/letsencrypt' but with another content:
#!/bin/bash
/usr/bin/letsencrypt renew --renew-hook "/etc/init.d/nginx reload"
Step 6 - Test SSL configuration
When we are done with the configuration it's time to take a cup of coffee and relax and test our configuration. There are dozens of options to test SSL, but I will use two, the first one is curled:
curl -vI https://ssl.itsyndicate.org
* Server certificate:
* subject: CN=ssl.itsyndicate.org
* start date: May 3 15:44:12 2022 GMT
* expire date: Aug 1 15:44:12 2022 GMT
* subjectAltName: host "ssl.itsyndicate.org" matched cert's "ssl.itsyndicate.org"
* issuer: C=US; O=Let's Encrypt; CN=Let's Encrypt Authority X3
* SSL certificate verify ok.
The second option is to open your site in Google Chrome and check the SSL certificate in the dev tool under the security tab:
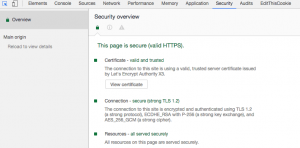
Conclusion
Now you know how to install Let's Encrypt SSL on Ubuntu 16.04 or Ubuntu 18.04 to secure your site. It is a very simple, useful, and cheap solution to protect your site and improve a bit your SEO rankings. If you have issues with installation or you want to save time - ask our technicians to maintain your server for you. Comments, improvements, and critics are always welcome!
Docker commands and Dockerfile usage for running containers on a local machine
Docker commands and Dockerfile usage for running containers on a local machine
Netflix tech stack for powering streaming backend and cloud solutions





